
Entering the European market for cybersecurity products and services
To enter the European market with cybersecurity products and services, you must comply with various laws and regulations, including the Cybersecurity Act. Buyers often have other requirements as well. The best way to enter the European market is by working with a strategic partner. Your strongest competition comes from Central and Eastern Europe (CEE) and Asia.
Contents of this page
- What requirements and certifications must cybersecurity products and services meet to be allowed on the European market?
- Through which channels can you get cybersecurity products and services on the European market?
- What competition do you face on the European cybersecurity products and services market?
- What are the prices of cybersecurity products and services on the European market?
1. What requirements and certifications must cybersecurity products and services meet to be allowed on the European market?
To enter the European market for cybersecurity products and services, you must comply with various mandatory (legal) requirements, and with other requirements from your buyers. Niche markets also have specific requirements. Requirements can vary per industry, per segment, and even per country.
General market entry requirements for IT and business process outsourcing (ITO and BPO) are listed in our study about the requirements outsourcing providers must meet. This chapter discusses the most common requirements for cybersecurity products and services. New legislation is constantly being developed, particularly around the European Green Deal (Europe’s roadmap to become a climate-neutral continent by 2050) and the digital transformation strategy of the European Union (EU). You should stay updated.
What are mandatory requirements?
When offering cybersecurity products/services in the European market, the following legal requirements may apply to you:
- Directive on the legal protection of computer programmes (2009/24/EC);
- General Data Protection Regulation (EU 2016/679);
- Data Act (EU 2023/2854) and Data Governance Act (EU 2022/868);
- ePrivacy Directive (2002/58/EC);
- General Product Safety Regulation (EU 2023/988);
- Artificial Intelligence Act (EU 2024/1689);
- Cyber Resilience Act (EU 2024/2847);
- Cybersecurity Act (EU 2019/881);
- NIS2 Directive (EU 2022/2555);
- Digital Services Act (EU2022/2065);
- eIDAS Regulation (EU 910/2014).
If you do not follow these rules, you may be subject to enforcement actions and/or possible claims. Being located outside of the EU does not mean these will not affect you.
Tips:
- Pay attention to copyright and infringement (the act of breaking or disobeying the contract) clauses in the contracts you sign with European buyers.
- Set up clear consent request forms and privacy policies that inform customers how you process their personal data. Keep records of your obtained consent.
- Stay informed about cybersecurity in the EU market by visiting the website of the EU Agency for Cybersecurity and reviewing the EU Cybersecurity Strategy.
What additional requirements and certifications do buyers often have?
European buyers of cybersecurity products and services often have the following additional requirements:
- A quality management system, often ISO 9001 or CMMI;
- An information security management system, preferably ISO 27001 compliant/certified;
- Agile project management methodologies.
Tips:
- Make sure you have effective security processes and systems in place, from business continuity and disaster recovery to virus protection.
- Consider obtaining ISO/IEC 27701 certification, which is an extension to ISO/IEC 27001 and ISO/IEC 27002. To certify, you need to either have an existing ISO 27001 certification or implement ISO 27001 and ISO 27701 together as a single audit.
- If you (aim to) specialise in particular sectors, find out which certifications are relevant. When considering a certification, ask yourself 3 questions before working out the details: Is it good for my company? Is it good for my clients? Does it have marketing value?
- Check if you can apply for financial support to achieve quality certification. Contact your national IT association (such as TAG Georgia or BPESA from South Africa) or a business support organisation in your country responsible for (IT) export promotion.
EU Cybersecurity Certification Scheme on Common Criteria (EUCC)
The EUCC is a voluntary certification framework for certifying the cybersecurity of ICT products. Its main goal is to raise the security standards for ICT products, services and processes available on the EU market. To achieve this, the framework has a complete set of rules, technical specifications, standards and procedures that must be consistently applied across the EU.
Through the EUCC, ICT suppliers can undergo a standardised, EU-wide recognised assessment process. This allows certification of various ICT products, including technological components, hardware and software. The framework is based on the SOG-IS Common Criteria evaluation framework, already used by many EU countries. The EUCC supports different assurance levels depending on the product’s security requirements.
The EU Agency for Cybersecurity (ENISA) is currently developing 2 other certification schemes: EUCS on cloud services and EU5G on 5G security.
Tip:
- Visit the ENISA EU Cybersecurity Certification website for more information on the development of certification schemes.
Up-to-date knowledge and skills
As European buyers expect you to work with the latest technology, you must stay informed about the latest platforms, frameworks and innovations and keep your skills up to date. Figure 1 and 2 give an overview of important skills and platforms needed for cybersecurity services and solutions.
Figure 1: Important cybersecurity services technology skills and platforms
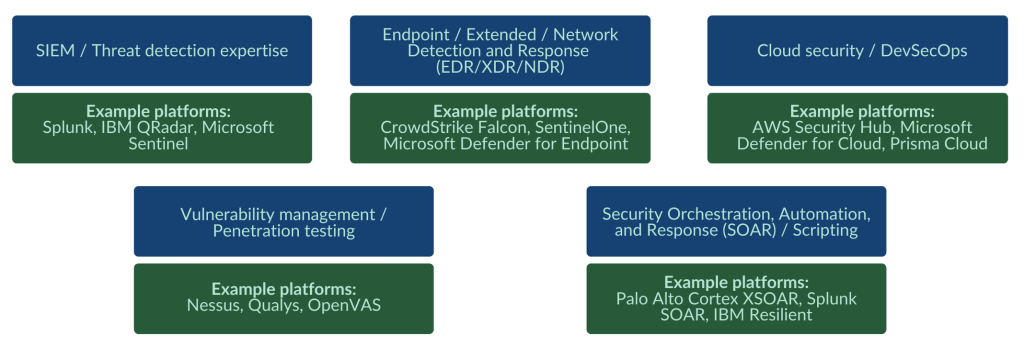
Source: Globally Cool
Table 1: Important cybersecurity solution development skills and platforms
| Cybersecurity skill area | Key platforms/tools |
|---|---|
Secure Software Development Lifecycle (SSDLC) / Threat Modelling |
|
| Cryptography / Identity and Access Management (IAM) Development |
|
| Cloud-native / Container security engineering |
|
| Security data processing / Integration (SIEM/SOAR APIs) |
|
| Security automation / Testing (CI/CD and DevSecOps) |
|
Source: Globally Cool
Tips:
- Continuously train your staff to stay up to date on the required software and hardware skills for your product/market.
- Provide references, testimonials and examples of recent work on your website. European companies often require proof of your technical skills.
- European buyers may expect you to work according to the Agile concept. This is based on the Agile Manifesto, representing the ability to respond to change. It focuses on how people work together, letting solutions evolve through collaboration between self-organising and cross-functional teams. Agile development advocates adaptive planning, visualisation, evolutionary development, early delivery and continual improvement.
Soft skills
Besides technical knowledge and experience, cybersecurity professionals must also have good soft skills. Clear communication helps them understand clients’ needs and improve collaboration. This also builds trust. Skills like problem solving and flexibility help developers tackle issues and adapt to project changes. Understanding what end users want and making software easy to use is also important. Good leadership and teamwork skills keep everyone on track and motivated, ensuring projects run smoothly.
Sustainability
Companies are more often required to demonstrate their socially and environmentally sustainable business practices. Voluntary standards like ISO 26000 (social) and ISO 14001 (environmental) can help you demonstrate that you are responsible.
Tip:
- Read about sustainability in ITO/BPO in our tips on how to go green and how to become more socially responsible in the outsourcing sector.
What are the requirements for niche markets?
Requirements for cybersecurity vary per industry and country. When planning to offer products or services in a specific niche, check the applicable requirements.
Applicable requirements per country
For country-specific information, check the national government websites. For example, if you plan to export to Germany, you must take into account the IT-Sicherheitsgesetz 2.0 (German IT Security Act), BSI Kritis Regulation (regulation for organisations with critical infrastructures) and TDDDG (Telecommunications Digital Services Data Protection Act). The BSI IT-Grundschutz is also an important German standard for information security.
Applicable requirements per industry
If you develop cybersecurity products or services for a specific industry, you need to take its specific requirements into account. For example:
- In the automotive industry, some standards and regulations are ISO/SAE 21434 and UN Regulation No. 155 on cybersecurity and cybersecurity management systems (CSMS);
- In the financial sector, relevant standards and regulations include the Digital Operational Resilience Act (DORA, EU 2022/2554), Payment Services Directive 2 (PSD2, EU 2015/2366) and Payment Card Industry Data Security Standard (PCI DSS);
- In the Internet of Things (IoT) sector, ETSI EN 303 645 (cybersecurity for consumer IoT) is an important standard.
Keep in mind that these are only some examples. The requirements for niche markets vary greatly, because the market is very diverse. There are a lot of technologies, and companies often focus on horizontal and/or vertical markets. So you have to research your specific situation, market, and requirements.
Tip:
- Check which sector-specific standards or codes are available for your product (for example, by asking your sector association or your buyer) and to what extent your buyers want you to implement them.
2. Through which channels can you get cybersecurity products and services on the European market?
The European cybersecurity market can be divided into several segments: cybersecurity services, cybersecurity solutions, industry verticals, threat type and deployment type. You can tap into these segments through several market channels. The most realistic channel for you is working with a strategic partner.
How is the end market segmented?
The market for cybersecurity can be segmented in multiple ways: cybersecurity services, cybersecurity solutions, industry verticals, threat type and deployment type.
Figure 2: Market segments in the cybersecurity market
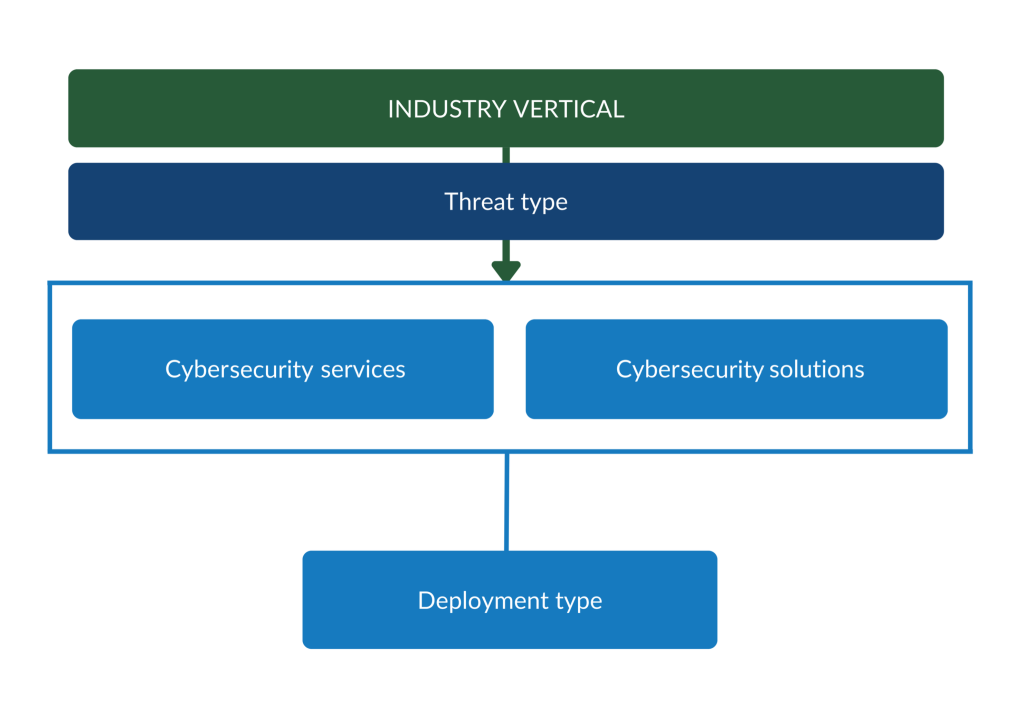
Source: Globally Cool
Cybersecurity services refer to professional offerings like consulting, managed security services, training in firewall management, risk assessment and vulnerability management services. In Europe, the cybersecurity services segment leads the market with a projected value of €21.94 billion in 2025. Companies operating in the European market include Orange Cyberdefense and NCC Group.
Cybersecurity solutions consist of hardware and software tools that protect digital systems and data. These include firewalls, endpoint protection, Identity Access Management (IAM) and encryption solutions. These tools help organisations to defend against unauthorised access and cyberattacks. Companies offering cyber solutions in the European market include Cyber Detector and WithSecure.
Industry vertical segmentation divides the market by end-user industry. Sectors include healthcare, retail, manufacturing, automotive, and Banking, Financial Services and Insurance (BFSI). Each sector needs tailored cybersecurity solutions due to specific operational, regulatory and infrastructure needs. Sectors with high maturity in the EU include electricity, telecoms and banking. Sectors that are in a risk zone – sectors with a relatively low maturity compared to their criticality – and need more attention include:
- ICT service management;
- Public administration;
- Health;
- Maritime;
- Space;
- Gas.
Threat type segmentation focuses on solutions or services designed to prevent specific cyberthreats. These threats include malware, phishing, ransomware and Advanced Persistent Threats (APTs). They require specialised defences based on their method and impact. In the EU, the most common threat types in 2023-2024 were DoS, DDoS and RDoS, accounting for 46% of all cases. This was followed by ransomware attacks (27%) and data-related threats (16%).
Deployment types describe how cybersecurity solutions are delivered and implemented. They can be used on-site, via the cloud or by using a hybrid model. According to Statista, cloud security is developing the fastest.
Positioning your company as a specialist in specific segments strengthens your offer as a provider of cybersecurity services or solutions.
Tips:
- Specialise in a particular industry. Industries with specific security needs, for example because they deal with highly sensitive personal information, require specialists rather than generalists.
- Research the segment that you want to focus on to effectively market your company.
Through which channels do cybersecurity products and services land on the end market?
Figure 3 provides an overview of the trade channels you can use to enter the European market. This structure is very similar in every country. Working with a strategic partner is your most realistic option.
Figure 3: Trade structure for cybersecurity products and services in the European market
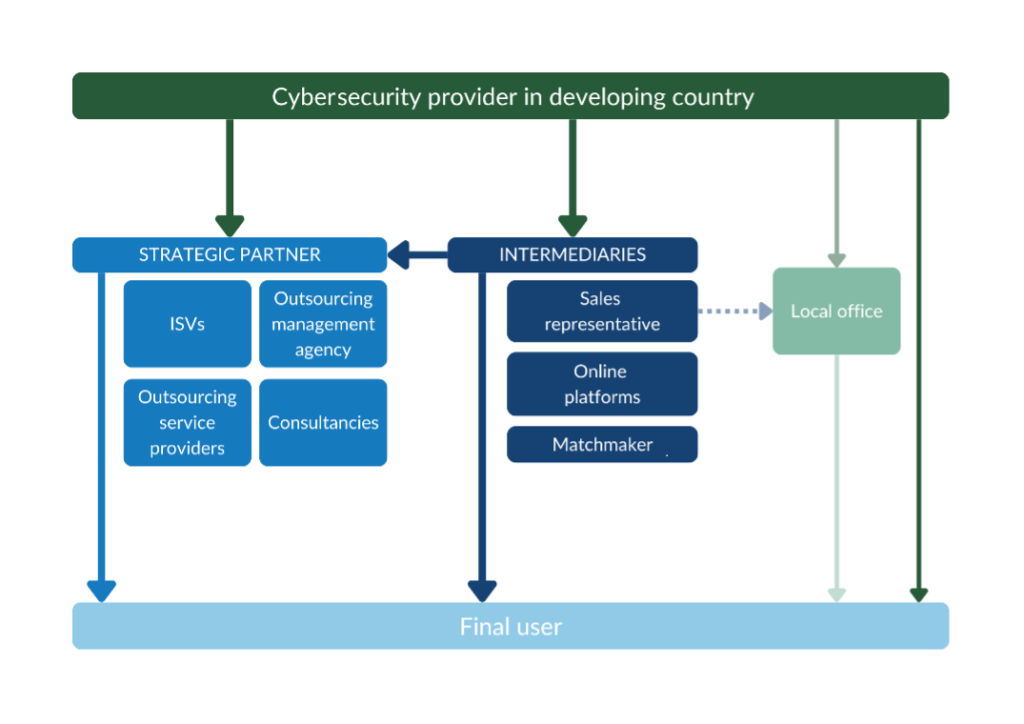
Source: Globally Cool
Strategic partners
Working with a strategic partner is your most promising market entry channel. This could be Independent Software Vendors (ISVs), outsourcing management agencies, outsourcing service providers, or consultancies.
A provider that is similar to your company (for example in terms of size, technology portfolio and customer portfolio) would be most suitable. Ideally, this company should develop, market, sell, and maintain cybersecurity products and/or services.
The relationship between a strategic partner and a subcontracted supplier (you) is generally characterised by:
- Trust;
- Interdependence;
- A structured relationship (functions, tasks, communication, and procedures);
- Potentially limited marketing visibility and market access opportunities for the subcontracted supplier;
- No intellectual property (IP) rights, or a loss of IP rights for the subcontracted supplier.
Please keep in mind that when you work with a strategic partner, they communicate with the final user about the cybersecurity product or service being provided. You are only a subcontractor and will probably not appear in their marketing communications. You will be referred to as ‘delivery centre’.
You can find a strategic partner either directly or by working with an intermediary. Because many European companies prefer to deal with a local contact person, an intermediary is a good option.
One company that established a partnership to enter the European market is Brazilian-based Syhunt, offering application security solutions. In 2024, it appointed the Portuguese company Cyberjump to act as its distributor in Portugal and Spain. Cyberjump is a distributor of specialised cybersecurity and AI solutions.
Tips:
- Attend relevant (online) industry events like the Gartner Security & Risk Management Summit and Infosecurity Europe to meet potential partners and competitors. Do your homework and select events that fit your profile. Make a list of relevant events using directories such as 10Times.
- Use industry associations or outsourcing associations to find potential customers in Europe. See for example the member list of Cyberveilig Nederland.
- Use general IT industry associations to find potential customers, such as Bitkom in Germany, NLdigital in the Netherlands, and techUK and BIMA in the UK.
Intermediaries
You can work with an intermediary to find a buyer or strategic partner.
Matchmakers
A matchmaker is a person or a company with many relevant contacts in a specific market segment. They do not make cold calls. Always properly inform your matchmaker about your company, so they can match you with suitable leads from their network.
If you work with a matchmaker:
- They make appointments with prospects for you;
- Presentation and sales process remains your responsibility;
- You often pay a retainer plus success fee;
- They often have multiple clients;
- You need to set clear expectations and objectives (and exit criteria) to measure their performance.
A retainer plus success fee can be expensive. The success fee depends on what the matchmaker has delivered, but you must pay the retainer (usually a fixed monthly payment) regardless of their performance. The retainer should be high enough to cover some of the costs, but low enough to encourage delivery. A lawyer must draft the contract.
You also need to include a trial period (usually ≤3-4 months) after which the contract can be terminated without further consequences. The delivery expectations and targets for this initial period must be clearly defined, such as the number of relevant contacts, meetings, and leads. Your contract should also have clear exit options.
Sales representative
Another type of intermediary is a sales representative. These representatives are more involved in the sales process than matchmakers.
When working with a sales representative:
- They contact prospects for you;
- They also make the sales and sometimes manages projects to a certain degree;
- You often pay a retainer plus success fee (which can be expensive) or a fixed monthly fee;
- They can have multiple clients or work exclusively for you.
A good sales representative has a large, relevant network, so they do not make cold calls. Their success fee is often a percentage of the value of the projects they bring in.
Online platforms
Electronic marketplaces are a cheap marketing tool that may make direct sales easier. These platforms used to focus on freelancers, but some serve SMEs now too.
Tips:
- Make sure that any selected matchmaker or sales representative has a large relevant business network.
- Be cautious if intermediaries only ask a success fee, because either they are excellent at their job, or they are desperate and may not (be able to) deliver. You should also be cautious if intermediaries want to work for you part-time besides their regular job, because they are often too busy to deliver.
- Work with a good lawyer who knows the laws of the country where the intermediary resides and has experience with this type of contracting. Pay special attention to exit clauses, success criteria, deliverables, and payments.
- Look for leads on online platforms like UpWork, Freelancer, Fiverr, ITeXchange, Clutch and pliXos. For more information on online marketplaces, read our study about finding buyers on the European outsourcing market.
Local office
Another option is to establish a local office in your European target market. You can also open an office in one of Europe’s nearshoring destinations (like CEE). This is often cheaper.
A local presence makes it easier to build up long-term relationships with customers through personal contact. It also increases your credibility, builds trust and allows you to retain complete control over your marketing and sales activities. However, this can be difficult, as it requires a lot of experience and large investments. Many IT service providers in developing countries are simply too small and do not have the financial strength or enough verified market opportunities for this.
Tips:
- Consider establishing your own office if you already have a client base in the target market, or if you have a well-founded indication of the demand for your services/products. If you decide to establish an office, involve your sales/marketing representative.
- Be aware that establishing a local sales office is very costly and you need a strong financial position.
- Look for alternatives to lower your costs, such as business incubators or government incentives to bring your business to a particular country/region.
Direct sales
You can also try to sell your cybersecurity services directly to European end users. Many European companies are looking for cost reduction and delivery capacity, which developing countries can often provide. This is 1 of your unique selling points – or at least a competitive selling point. However, you should be aware that these end users might not have qualified IT staff to work with. Also, European companies are generally hesitant to outsource their security processes, especially through offshoring.
Direct sales require experience in the European market and are most suitable for relatively large providers that want to target large European end users. Your best option is to focus on a small, underserved niche market. But for most suppliers from developing countries, it is very challenging to sell cybersecurity services directly. Having existing customers in Europe will help, as references are a must for direct sales.
Tips:
- Combine offline and online promotion channels to develop as many contacts as possible. This maximises your chances of finding suitable partners/customers. Use social media platforms as a marketing tool to reach potential customers. LinkedIn can be particularly useful for making initial contacts and conducting market research.
- Build a professional, high-quality company website, where you present full, accurate, and up-to-date details of your product/service offering. Make it compatible with mobile devices and invest in Search Engine Marketing and Search Engine Optimisation, so potential customers can easily find you online.
What is the most interesting channel for you?
The most promising market entry channel is to provide cybersecurity solution development services to strategic partners in Europe. But selecting the right channel depends on your type of company, the nature of your service, your target market, and the available resources for market entry. Regardless of the channel you choose, your own marketing and promotion is a very important part of your market entry strategy, for which you are responsible.
Tip:
- Decide on a business model and create your ideal client persona. It helps you to tailor your offer.
3. What competition do you face on the European cybersecurity products and services market?
European end-user companies often prefer outsourcing to providers within their country. Especially smaller companies outsource cybersecurity tasks locally. But European ITO providers often subcontract to nearshore and offshore outsourcing companies. They often prefer nearshore locations because of proximity, language, cultural similarities and the minimal time difference.
Which countries are you competing with?
European companies often prefer to outsource to nearshore destinations. This is especially true for cybersecurity, which means your main competitors are based in Europe. Important competing countries include those in CEE. They offer a strong mix of tech hubs, skilled talent and competitive costs compared to Northern and Western Europe, high English proficiency, minimal time differences and cultural alignment. You also face competition from major offshore outsourcing leaders like India. Vietnam is another important player.
The Global Services Location Index (GSLI) shows countries’ attractiveness as an offshore location for ITO/BPO services. It ranks their competitiveness based on 4 categories:
- Financial attractiveness;
- People skills and availability;
- Business environment;
- Digital resonance.
Based on the GSLI, India is the most attractive ITO/BPO destination. Vietnam also has a high position, ranking 7th. CEE countries and Ukraine score lower but are leading outsourcing locations for European companies.
Source: Kearney, 2023
CEE countries: Preferred nearshoring destinations
Companies from CEE have a positive image in the European market and are often seen as a safe choice. CEE countries are important outsourcing hotspots because of their skilled talent and geographic and cultural proximity to Northern and Western Europe. Also, being part of the EU gives them advantages in legal compliance and easier business integration when serving European clients.
Especially in cybersecurity, trust is very important. European companies prefer to outsource to countries they know well, so they often nearshore to other European countries rather than offshore farther away. Rates for cybersecurity services are higher than in offshore destinations. However, this generally does not deter European buyers, who are often prepared to pay for the benefits of nearshoring.
Cybersecurity companies from CEE can also apply for a Cybersecurity Made in Europe Label. This is a marketing tool created by the European Cybersecurity Organisation (ESCO). It highlights the value of cybersecurity companies that come from Europe and build their business on trustworthy European values.
Poland
Poland ranks 13th on the GSLI 2023. It is a large supplying country with a big pool of IT professionals. It has many higher education institutions, including 40 state universities and 20 public technology institutes. They have trained around 400,000 IT specialists. Polish IT specialists have experience working with international companies and are skilled in advanced technologies. The HackerRank shows that Poland’s programmers are among the best in the world. Polish also score very high on English proficiency, making it relatively easy for European clients to communicate with them.
Poland also has a cybersecurity cluster #CyberMadeInPoland. It has 66 members and brings together the private sector, public administration, industry chambers and international corporations. Together, they want to advance the Polish cybersecurity sector and promote Polish companies in the international market. Poland is also home to the biggest cybersecurity trade fair in CEE, the Cybersec Expo & Forum.
Czechia
Czechia is another well-known nearshoring destination. There are more than 221,000 Czech ICT professionals. Czech developers are rated as the ninth-best developers in the world. They are also among the best in the world when it comes to the security domain, ranking fourth on the HackerRank. According to Statista, Czechia is emerging as a European leader in cybersecurity. This is driven by a rising number of innovative startups and a strong emphasis on research and development. Czech people are also highly proficient in English. This makes Czech developers strong competition for you.
However, the industry faces a challenge: attracting new employees. After Germany, Czechia is the EU country facing the greatest challenges in filling ICT specialist vacancies (70.5% in 2024). This may drive Czech software companies towards subcontracting.
Romania
Romania holds the leading position in Europe and sixthworldwide for certified IT specialists per 1,000 inhabitants. The country has a large tech workforce of 120,000 programmers and more than 360 custom software development companies. Around 25,000 students (7% of all applicants) enrol in computer science programmes every year across nearly 100 universities.
Bucharest is Romania’s main IT hub, holding 63% of the country’s software development revenues. Other key cities are Cluj-Napoca, Timișoara and Iași. These hubs have research centres and innovation clusters focused on, among others, cybersecurity, AI and cloud technologies. Romania is building a reputation in important domains like cybersecurity and AI. Well-known Romanian cybersecurity companies are Bitdefender and TypingDNA.
Romania ranks high on the English proficiency index; English is the primary working language among Romanian tech companies. Also, Romania is known for its exceptional price-to-quality ratio.
Growing challenges in CEE are rising costs and talent shortages. The success of the tech sector has driven up talent competition and salaries in major hubs. The increased rates have made the cost gap with Western Europe smaller. Also, being in the EU means businesses face higher operating costs than some offshore locations. This is why some CEE companies subcontract work to offshore destinations.
India: Low-cost destination, service providers increasingly integrate AI
India continues to lead the GSLI with its combination of low-cost services, high English proficiency and a skilled workforce. This makes it a strong competitor in the IT outsourcing market. India has a young and fast-growing workforce. To stay ahead, the country must make the transition from lower-skilled jobs that can be replaced by robots to more creative and high-skilled work. Technological advancements and socioeconomic changes will reduce India’s labour cost advantage. This also applies to other low-cost countries.
India is usually regarded as a ‘bulk’ destination. Buyers often link extremely low developer rates in Asian countries to poorer project quality. They assume that cheap service providers must be using less skilled or less experienced developers, or that working conditions must be poorer.
Looking at cybersecurity in particular, India’s cybersecurity ecosystem consists of over 400 companies. Most of these companies are located in the following hubs: Bengaluru, Pune/Mumbai and Delhi/NCR. India’s cybersecurity sector is maturing. The number of providers that focus on innovative solutions – both established players and startups – is growing.
Cybersecurity service providers are more often integrating generative AI (GenAI) to automate processes and improve threat management efficiency. In 2024, around 35-40% of the service providers had incorporated AI into their offerings. To speed up AI adoption in cybersecurity, service providers are forming strategic partnerships and industry collaborations. This approach has become more important because of the complexity of GenAI solutions.
Vietnam: Relatively young, but strong outsourcing destination
Vietnam is a strong outsourcing destination, ranking seventh on the GSLI. Compared to India, the Vietnamese outsourcing industry is relatively young. But because of the presence of large technology companies, Vietnam is considered a global digital hub. This also stimulates the country to keep improving the skills of its workforce.
An example of a large company operating in Vietnam is the Viettel Group. In 2025, Viettel Cyber Security introduced its ‘Make it Vietnam’ cybersecurity solutions to the European market. The company wants to enter the European market and partnered with the French company InnoSynthex to do so.
Viettel Cyber Security will bring its strong technological capabilities and cybersecurity expertise, offering services like advanced threat intelligence updates, penetration testing, and vulnerability assessments. InnoSynthex will complement the partnership with its established European client base and experience in security solutions that adhere to GDPR and ISO 27001 standards.
But according to Vietnam’s National Cybersecurity Association, Vietnam will probably have a shortage of 700,000 cybersecurity professionals in the short term. Among the reasons for the talent shortage is that many skilled Vietnamese professionals work for foreign companies and there are not enough institutions specialised in cybersecurity education.
Although Vietnamese people generally have low English proficiency, most Vietnamese cybersecurity specialists have intermediate to upper-intermediate English language skills.
Ukraine: Increased cooperation with the EU on cybersecurity
The technology sector is an important pillar of Ukraine’s economy, ranking second in exports and contributing 4.4% to the gross domestic product (GDP). Ukraine has 2,118 tech companies. About half of them provide services, of which 47% are focused on outsourcing and 3% on outstaffing. Most of the tech companies are located in Kyiv, followed by Lviv and Kharkiv. Ukraine has 302,000 professionals in the tech industry, of which 238,000 are working within the country. The average salary for a tech specialist is €2,257.
In the cybersecurity area, the EU and Ukraine have deepened their cooperation. In November 2023, ENISA signed a working arrangement with the National Cybersecurity Coordination Center (NCCC) and the Administration of the State Service of Special Communications and Information Protection of Ukraine (SSSCIP). This cooperation focuses on cyber awareness and capacity-building, best-practice exchange, and knowledge sharing to increase situational awareness. This was ENISA’s first working arrangement with a non-EU country.
Ukraine is also part of the EU initiative CyberEast and CyberEast+, has regular Cyber Dialogues with the EU, and was granted access to the EU Cybersecurity Reserve for rapid operational support during large-scale cyberattacks. Ukraine also has a strategic partnership with the UK – the UK-Ukraine TechBridge – to strengthen ties between their tech ecosystems, including cybersecurity. The strong cooperation makes it easier for Ukrainian companies to work with European companies.
In cybersecurity, Ukraine’s expertise lies in R&D and developing innovative solutions. Their most important segment is network security. But some segments are increasing at a fast pace: cloud security, data protection and endpoint security.
Despite the war, around 85% of the Ukrainian developers managed to keep working, either in Ukraine or abroad. Outsourcing software companies have taken measures to continue business during the war, like relocating employees to safer areas, diversifying talent recruitment globally, and independent internet solutions. Also, quite a few Ukrainian tech companies are opening offices abroad. IT Research Ukraine states that 51% of CEOs want to expand their business. Of these, over one-third want to set up branches abroad. Poland is the preferred choice of expansion.
Tips:
- Compete on the quality of your services, rather than just on costs. Specialise in specific vertical markets and/or niche market segments to minimise competition.
- Invest in country branding. For more information, see our tips on how to do business with European buyers.
Which companies are you competing with?
Some cybersecurity companies are:
IARM Information Security (India)
IARM Information Security is a cybersecurity company that was founded in 2015. It has offices in India, the United States and Singapore, and clients in 15 countries across the world. It provides a wide range of cybersecurity services including:
- Professional services like cloud security and Large Language Models (LLM) penetration testing;
- Managed security services like Security Information and Event Management (SIEM) solutions;
- Industrial cybersecurity like Internet of Things (IoT) security and embedded cybersecurity solutions.
Cyber Security Consulting (Czechia)
Cyber Security Consulting is a Czechia-based cyber security consulting company. It has ample experience working for clients from Czechia and abroad. The services it offers include penetration tests, purple teaming, application security design, security assessments, security consulting, and cybersecurity awareness.
CyRadar (Vietnam)
CyRadar is an innovative cybersecurity company in Vietnam. They use new technologies like AI, machine learning (ML) and Big Data to bring a new approach to cybersecurity solutions. They offer a variety of products and services to their clients, like advanced threat detection, endpoint detection and response, pentest and Next-Gen Security Operations Centre (SOC).
Berezha Security Group (Ukraine)
Berezha Security Group is a cybersecurity company in Ukraine, with an office in Poland as well. They specialise in application security and penetration testing services, delivering across sectors like banking, fintech, retail and healthcare. Their mid and senior-level consultants all hold leading certifications like OSCP (Offensive Security Certified Professional), CISSP (Certified Information Systems Security Professional) and CISA (Certified information Systems Auditor) to demonstrate their expertise in cybersecurity.
Tip:
- Learn from competitors that operate in the European market. Compare them on aspects like price, their offer, and the segments and industries they focus on.
Which products are you competing with?
Everything that is connected to the internet needs cybersecurity measures. There are no products to compete with. The real question here is: what makes one service provider different from another?
The answer is technical knowledge, available capacity, references, domain knowledge, flexibility, scalability, reliability, communication and language capabilities, quality management, infrastructure, vertical and/or horizontal market focus and niche market orientation, among other things. The location (country) of the service provider is also an important factor.
Tip:
- Look at cybersecurity companies that have successfully entered the European market. See how they position and promote themselves. Find out how you can get a competitive advantage, based on factors like quality, cost, technology or product characteristics.
4. What are the prices of cybersecurity products and services on the European market?
Although price is often not the most important selection criterion for cybersecurity services, it has to be right and competitive. The price for cybersecurity products and services is influenced by technological requirements, skill levels, complexity of the project, length of the contract, and other requirements written in the Service Level Agreement (SLA).
Your offer should include the price, with your hourly rates and an honest estimation of the number of hours you expect to work on the project. You must also choose a price model for your product or service.
The most popular pricing models for cybersecurity services are:
- Time and Material (T&M);
- Monthly recurring (retainer-based/managed services);
- Pay-per-use/Consumption-based;
- Hybrid models: a combination of fixed and variable elements.
The most popular pricing models for cybersecurity solutions are:
- Fixed-Price;
- T&M;
- Hybrid models: fixed and T&M.
The most common price model for cybersecurity solutions is a Fixed-Price contract. This is an all-inclusive offer, where clients are billed based on pre-defined milestones (in the SLA).
If you focus on a niche market, European buyers are often less price sensitive.
Tips:
- Study average prices, for example, via IT Jobs Watch. You can also research average salaries via platforms like Payscale or Glassdoor.
- Create the ’ideal’ client persona to help you tailor your offer. An example of a client persona is: ’a cybersecurity company with fewer than 200 staff members, in the Munich area, specialised in security applications for consumer IoT devices’.
- Go beyond setting the right price and work out your pricing strategy. This could include, for example, your preferred pricing model, payment terms and expectations, and how/when you offer discounts.
Globally Cool carried out this study in partnership with Laszlo Klucs on behalf of CBI.
Please review our market information disclaimer.
Search
Enter search terms to find market research
